WinAntiDbg0x100
Morning, everyone! Yeah, yeah, I know—nothing too special today, just a simple write-up on a simple challenge. So, let’s get started.
As I mentioned, I’ll be posting CTFs and crackmes, and this is the beginning i think👀👀.

As the name suggests, 0x100, this challenge is going to be pretty simple. I’m going to use IDA to show a block of the code, but for the most part, I’ll be using x64dbg.
I’ll start by decompiling the software and heading straight to the main code block. And guess what? I found a beautiful IsDebuggerPresent function call.
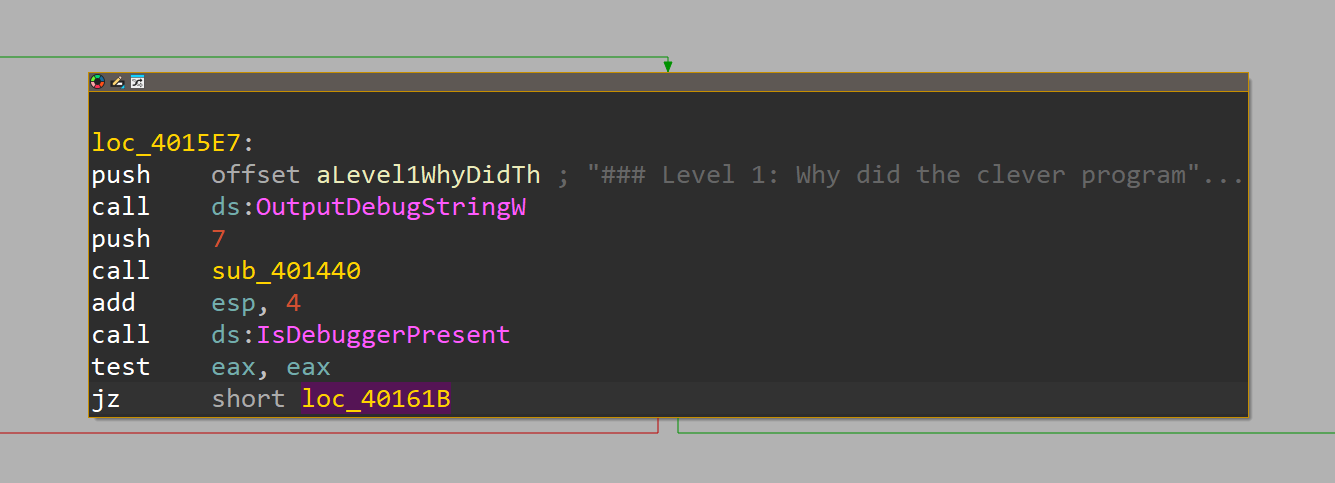
call IsDebuggerPresent
test eax, eax
jne debugger_detectedOkay, now in most of the cases you’re mot going to find a direct call to IsDebuggerPresent function, but you can find a call to IsDebuggerPresent function in the ntdll.dll library. But still, as i just said is a pretty simple challenge, therefore it means that in most of the cases that function may not be implemnte in the software or it may be there as an decoration.
Let’s get back to our beautiful block of code. As we can see though IdaPro , there is already set a debug detector that would push offset aOopsTheDebugge ; which seems to hold a set of characters but it reminds us that our debugger was detected.
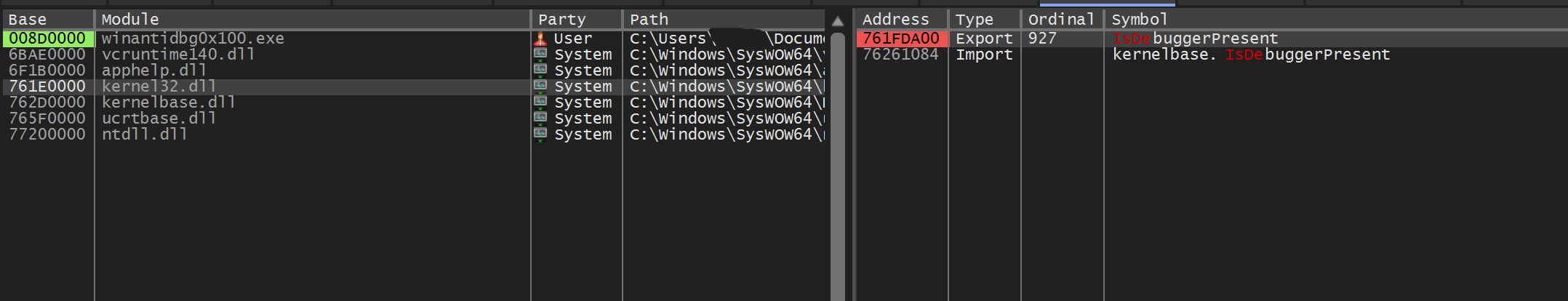
Calling x32dbg…
Now let’s move to x32dbg at the symbols tab where we can see the symbols of our exe. Now before moving to out next stuff lets define what is this thing. Symbol files hold a variety of data which are not actually needed when running the binaries, but which could be very useful in the debugging process. Therefore we can find the functions that are used in our exe. As we know IsDebuggerPresent() checks BeingDebugged flag that is contained in our PEB.
But that’s not really important for now but it’s important to know is a kernel function therefore we have to search for it in kernel32.dll.
By pressing F2 we set a breakpoint when the function is called.
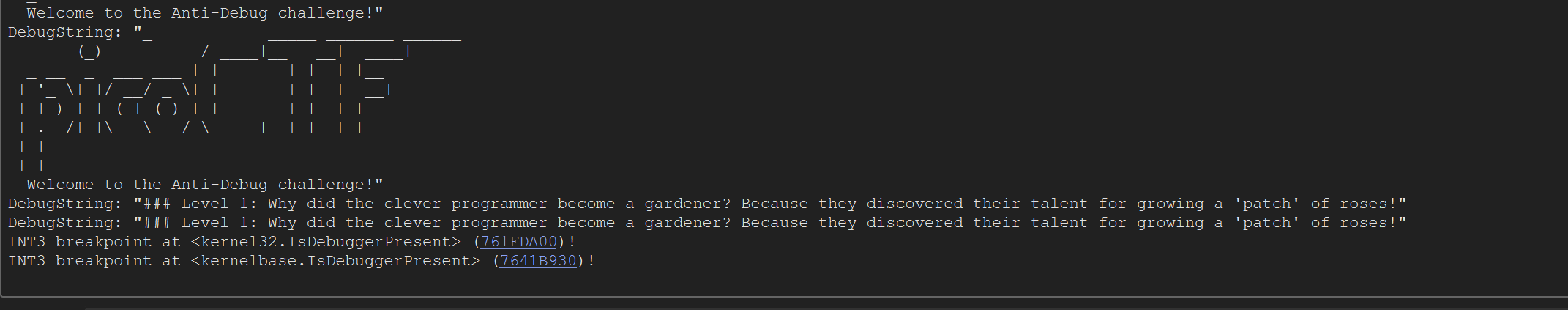
Thanks to our log tab we can see the memory address where the calling is made. As i wrote at the top of our blog we can see that IsDebuggerPresent consist of a call and a test , je being a result after test (Bitwise operation - AND). So if we want to patch we have just to patch it with jmp therefore we just pass the block of code that is executed if our flag is 1 (debugger detected).
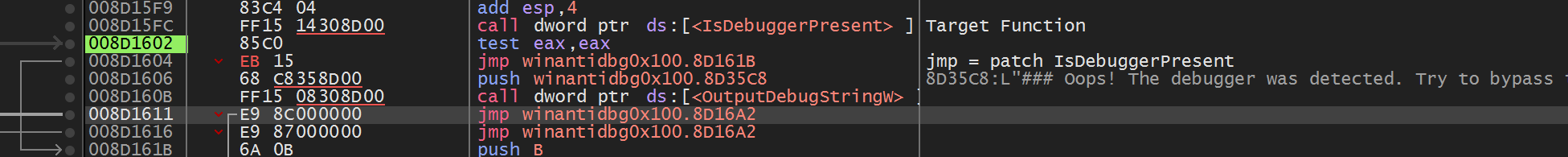
Ctrl-P to compile our new exe and after we execute we can see it works :)
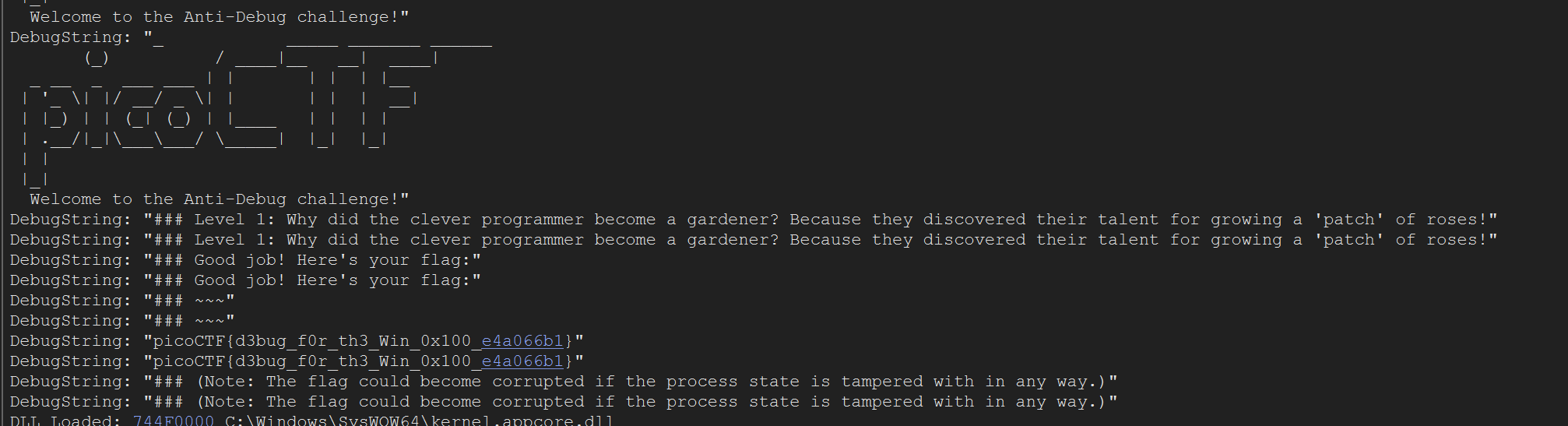
That’s it for today, folks! I hope you enjoyed this simple write-up. I’ll be back soon with more CTFs and crackmes but for now, I’m off to bed. Goodnight!
P.S. Sorry for choosing such a simple thing. :>
Would you like to support me?
If you find my content helpful and would like to support my work, consider visiting my Patreon page.
Your support means the world to me and helps keep this work going!

